Preventive measures to secure Data in AWS S3
Amazon Simple Storage Service is a fundamental component of Cloud Computing that is secure, scalable, durable, and highly available. It was the first service launched by AWS in 2006. It has been a building block for more than 175 services that AWS now offers.
Amazon Simple Storage Service is storage for the Internet.
It has a simple web services interface that you store and retrieve any amount of data, any time, from anywhere on the web.
New services in AWS like Redshift, Athena, EMR, and Lake Formation have made S3 not just a way to store objects but an engine for turning that data into insights.
Please refer to the below link to go through S3 Fundamentals: https://docs.aws.amazon.com/AmazonS3/latest/dev/Introduction.html
Today, S3 is used by millions of customers to store trillions of objects. From the beginning, massive focus for the service was on data security for data stored within it.
In this blog, we will see the best security practices to follow to secure data.
Security Best Practices fall under 2 categories:
In this blog, I will cover:
Amazon S3 Preventative Security Best Practices
1. Ensure to use correct Policies for S3 buckets and not to make them publicly accessible
-
Assign S3 bucket policies and Bucket Access Control Lists (ACLs) that provide read, write, or full-access to “All” or “Any authenticated AWS user.”
Sample S3 Bucket Policy
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": ["arn:aws:iam::123:user/ABC ", "arn:aws:iam::111122223333:root"] }, "Action": "s3:*", "Resource": ["arn:aws:s3:::mybucket", "arn:aws:s3:::mybucket/*"] } ] }This S3 bucket policy enables the root account 123 and the IAM user ABC under that account to perform any S3 operation on the bucket named “mybucket”
-
Amazon S3 Block Public Access
If an object is written to an S3 bucket with S3 Block Public Access enabled, it will block any type of public permissions via ACL or policy assigned to that object. It is an excellent second layer of protection to ensure that you don’t grant broader access to objects than intended.
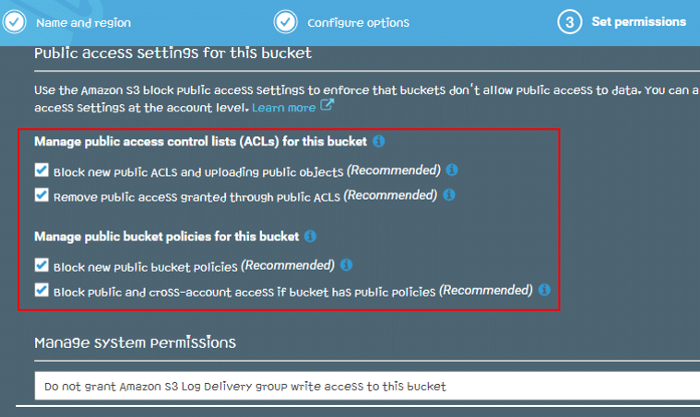
-
Use Trusted Advisor Service to inspect the Amazon S3 implementation.
It sends notifications to you of any open buckets at no cost to you.
2. Implement least privilege access
Implementing least privilege access is fundamental in reducing security risk and impact result from errors or malicious intent.
The following Access Control tools are available to implement least privilege access:
-
IAM User Policies and least Permissions for IAM Entities (“What can this user do in AWS?”)
IAM policies specify what actions are allowed or denied on what AWS resources. You can attach IAM Policies to IAM Users, Groups, or Roles, which are then subject to the permissions you’ve defined. In other words, IAM Policies define what a principal can do in your AWS environment.
-
Amazon S3 Bucket Policies (“Who can access this S3 bucket?”)
S3 bucket policies are attached only to S3 Buckets. It specifies what actions are allowed or denied for which principals on the bucket to which bucket policy is attached to (e.g. allow user ABC to PUT but not DELETE objects in the bucket).
** You attach S3 bucket policies at the bucket level which means you can’t attach a bucket policy to an S3 object, but the permissions specified in the bucket policy apply to all the objects in the bucket.
IAM policies and S3 bucket policies are both used for access control and they both are written in JSON using the AWS access policy language
-
Amazon S3 Access Control Lists (ACLs)
By default when a Bucket or Object is created in Amazon S3, default ACLs are assigned which grants the resource owner full control over the resource.
ACL Skeleton:
{ "ACL": "", "AccessControlPolicy": { "Grants": [ { "Grantee": { "DisplayName": "", "EmailAddress": "", "ID": "", "Type": "", "URI": "" }, "Permission": "" } ], "Owner": { "DisplayName": "", "ID": "" } }, "Bucket": "", "ContentMD5": "", "GrantFullControl": "", "GrantRead": "", "GrantReadACP": "", "GrantWrite": "", "GrantWriteACP": "" }Union of all the IAM policies, S3 Bucket Policies, and S3 ACLs that are applied to the Bucket serves the request to S3.
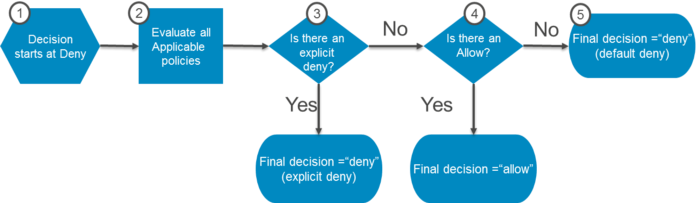
-
SCPs are organization policies that you can use to manage permissions in your organization. It offers central control over the maximum available permissions for all accounts in your organization. It helps you to ensure your accounts stay within your organization’s access control guidelines.
SCPs are JSON policies that specify the maximum permissions for an Organization or Organizational Unit (OU).
3. Multi-factor Authentication (MFA) Delete
MFA Delete can help prevent accidental bucket deletions. If MFA Delete is not enabled, any user with the password of a sufficiently privileged root or IAM user could permanently delete an Amazon S3 object.
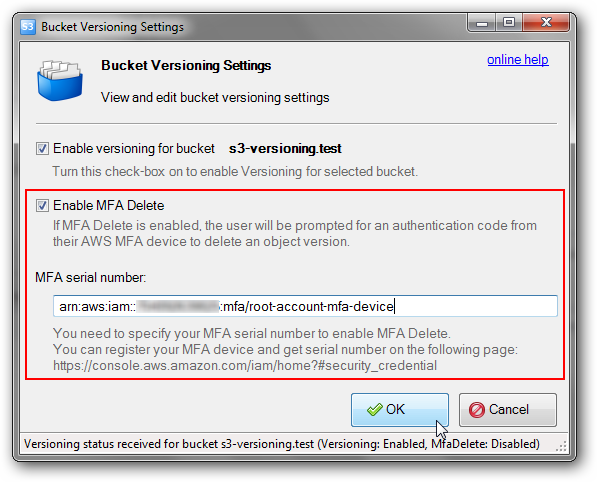
4. Encryption of Data at Rest
-
Server-Side Encryption- encrypts the object before saving it on disks in its data centers and then decrypts it when you download the objects. Server-Side Encryption can help reduce risk to your data by encrypting the data with a key stored in a different mechanism than the mechanism that stores the data itself.
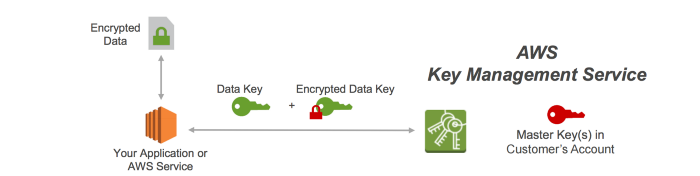
-
Client-Side Encryption- It encrypts data at client-side and uploads the encrypted data to Amazon S3. In this case, the client manages the encryption process, the encryption keys.
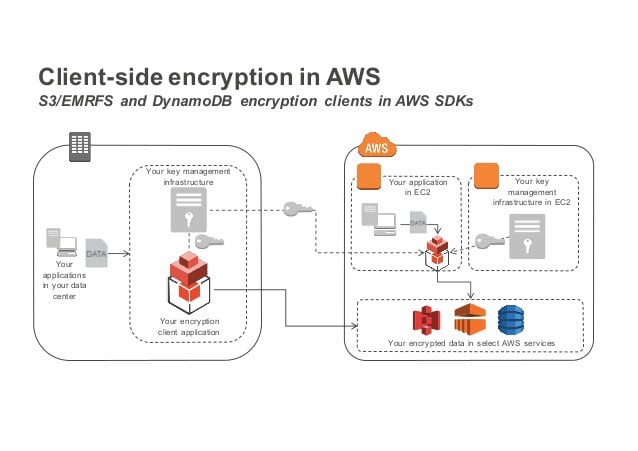
-
Default Encryption in S3- Amazon S3 default encryption provides a way to set the default encryption behavior for an S3 bucket. You can put default encryption on a bucket so that all new objects are encrypted when stored in the bucket. The objects are encrypted using server-side encryption with either Amazon S3-managed keys (SSE-S3) or customer master keys (CMKs) stored in AWS Key Management Service (AWS KMS).
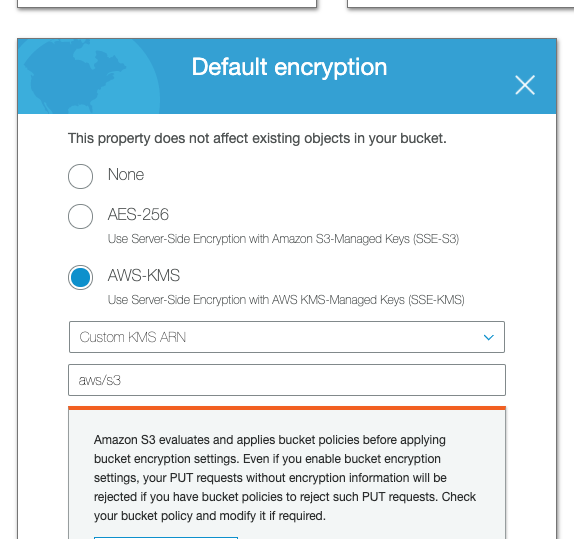
5. Enforce Encryption of Data in Transit
You can use HTTPS (TLS) to help prevent potential attackers from eavesdropping on or manipulating network traffic using person-in-the-middle or similar attacks. You should allow only encrypted connections over HTTPS (TLS) using the aws:SecureTransport condition on Amazon S3 bucket policies.
6. S3 Object Lock
S3 Object Lock enables you to store objects using a “Write Once Read Many” (WORM) model. S3 Object Lock can help prevent accidental or inappropriate deletion of data. For example, you could use S3 Object Lock to help protect your AWS CloudTrail logs.
Amazon S3 Object Lock provides two ways to manage object retention. The first is retention periods, and the second is legal holds.
-
A retention period specifies a fixed period during which an object remains locked. During this period, your object is WORM-protected and can’t be overwritten or deleted. You apply a retention period either in the number of days or number of years, with the minimum being 1-day and no maximum limit.
-
A legal hold provides the same protection as a retention period, but it has no expiration date. Instead, a legal hold remains in place until you explicitly remove it.
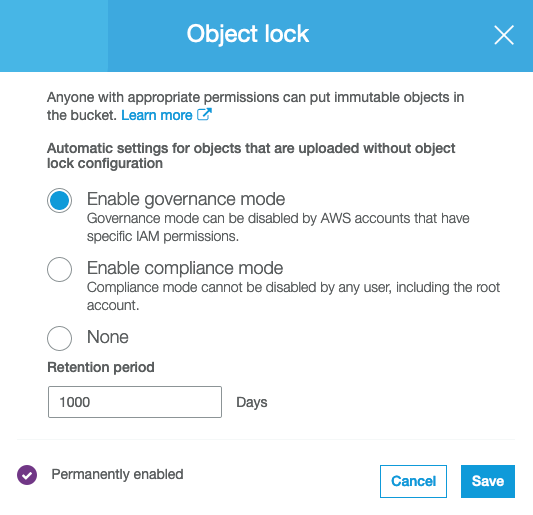
7. Enable Versioning
Versioning is a means of keeping multiple versions of an object in the same bucket. You can use versioning to save, retrieve, and restore every version of every object stored in your Amazon S3 bucket. It can easily recover from both unintended user actions and application failures.
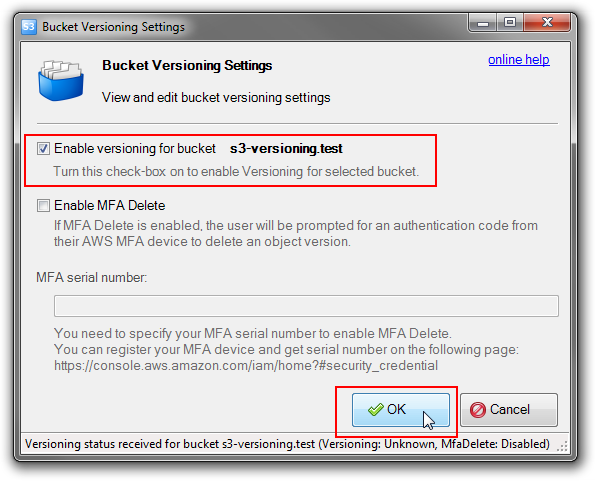
8. S3 Cross-Region Replication
CRR enables automatic, asynchronous copying of objects across buckets in different AWS Regions.
** CRR requires source and destination S3 buckets to have versioning enabled.
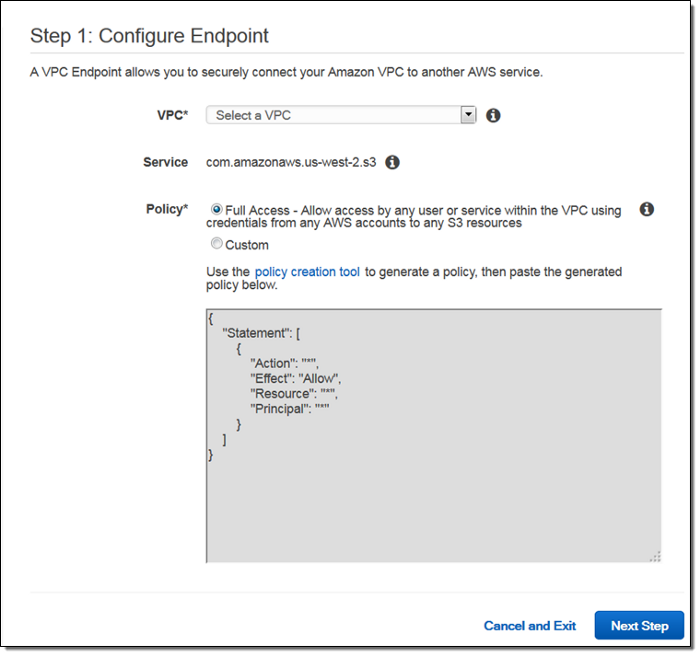
9. VPC Endpoints for Amazon S3 access
You can now access Amazon S3 from your Amazon Virtual Private Cloud (Amazon VPC) using VPC endpoints. Amazon VPC endpoints are easy to configure and provide reliable connectivity to Amazon S3 without requiring an internet gateway or a NAT instance. With VPC endpoints, the data between the VPC and S3 is transferred within the Amazon network, helping protect your instances from internet traffic.
It provides two additional security controls to help limit access to S3 buckets-
-> It requires that requests to your S3 buckets originate from a VPC using a VPC endpoint
-> It can be controlled what buckets, submissions, users, or groups are allowed through a specific VPC endpoint.
With the above security features of Amazon S3, you’ll indeed have good and better control over the security of your data in Amazon S3 other than in a typical on-premises environment. Also, check out our blog "Accelerate S3 Data Querying Performance with S3 Select" here.
Contact us at Clairvoyant for all your Cloud IT solutions requirements.