Securing AWS infrastructure from unauthorized attacks
Organizations these days are increasingly migrating their data to the cloud. AWS is one of the most popular cloud platforms for enterprises. It helps organizations save a lot of money and physical space regardless of whether the infrastructure is entirely on the cloud or the organization prefers a hybrid infrastructure.
Securing cloud infrastructure has become a big concern for organizations. At Clairvoyant, we employ AWS’s multiple security services to secure your AWS cloud infrastructure efficiently. We can help you enable these security services in your AWS account to expertly secure all your critical and sensitive data.
Protect & Detect
AWS Identity and Access Management (IAM) service securely manage AWS resources and services. IAM plays a critical role in the authentication and authorization of users and groups. It is the best cybersecurity practice and helps to ensure greater control of user access. You can use the IAM policy to grant and deny users and groups access to AWS services.
But IAM users and roles often carry the possibility of getting compromised. Resources such as EC2 instances can also get compromised due to cyberattacks.
How can organizations detect/monitor malicious activity and unauthorized behavior in such cases?
Each organization needs a way to detect malicious activity within its infrastructure. To detect cyberattacks or other unauthorized use, AWS comes with a few great security services which organizations need to enable in their AWS accounts.
Here are a few security services that AWS provides:
* Amazon GuardDuty * Amazon Detective * AWS Security Hub * Amazon Inspector
Let's explore them one by one:
GuardDuty
Amazon GuardDuty is a security service that helps detect threats. Amazon GuardDuty analyzes VPC Flow Logs, CloudTrail, and DNS logs. For near real-time processing of security detections, the service consumes large volumes of data. GuardDuty has built-in detection techniques.
Here is a GuardDuty dashboard that provides findings of security issues that struck the AWS environment. If you see, the below dashboard has been color-coded as blue, orange, and red as per the severity of the issue. This dashboard is extremely user-friendly and allows easy detection of any anomalies that find their way into the AWS account.
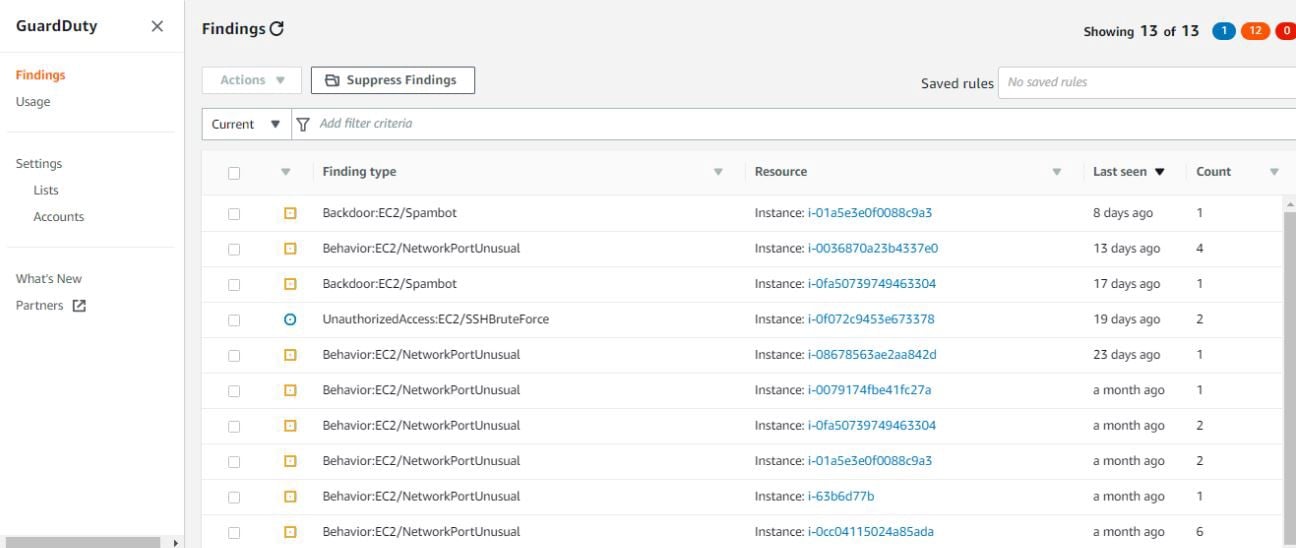 fig 2. GuardDuty findings
fig 2. GuardDuty findings
When you click on a finding, it expands to provide more information about it:
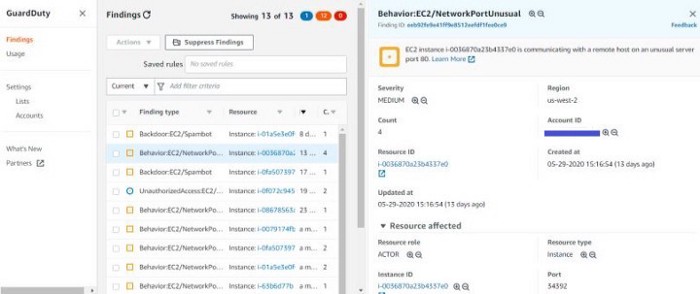 fig 3. GuardDuty findings in more details
fig 3. GuardDuty findings in more details
You can also whitelist and blacklist IPs for trusted and malicious IP addresses.
Detective
You can easily analyze, investigate, and identify suspicious activities using Amazon Detective. Amazon Detective collects log data and uses various algorithms to conduct security investigations more efficiently.
Amazon Detective analyzes VPC Flow Logs, AWS CloudTrail, and AWS DNS logs. Detective also processes Amazon GuardDuty findings for customers who have the Amazon GuardDuty enabled.
We can search for GuardDuty findings, AWS account, IP address, EC2 instance, AWS role, AWS user, and User-agent.
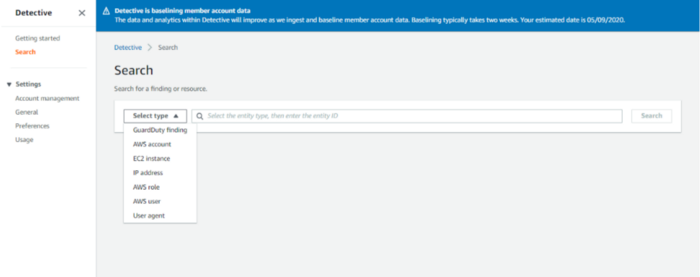 fig 4. Search types
fig 4. Search types
Detective shows information provided by GuardDuty in a much more readable format, with more details & visualizations:
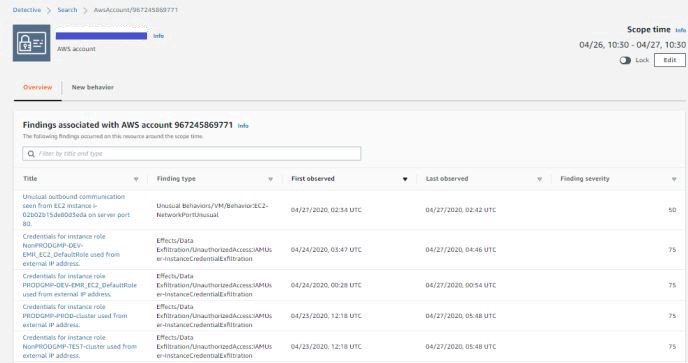 fig 5. Detective Findings
fig 5. Detective Findings
We can also obtain geolocation information on where in the world your AWS resources are being accessed from:
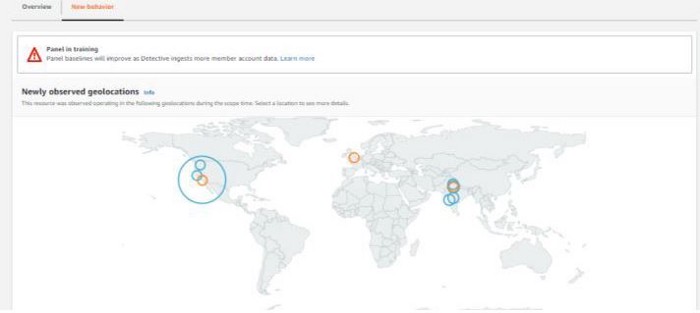 fig 6. Geolocation Findings
fig 6. Geolocation Findings
Inspector
Amazon Inspector allows you to test the network accessibility of your AWS EC2 instances. It also ensures the security of applications running on the EC2 instances.
Amazon Inspector analyzes the accessibility of your network configurations in AWS. Inspector agents are installed in the operating system of your AWS EC2 instances. Using Inspector, we can perform the Network and Host assessments.
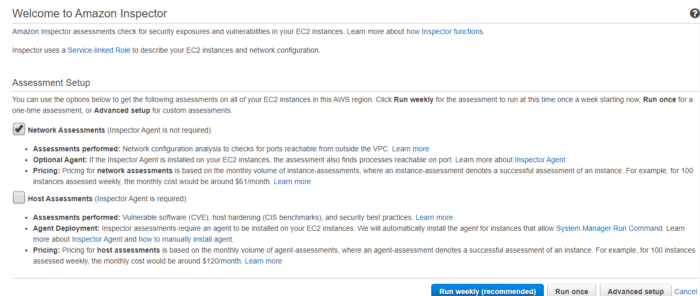 fig 7. Inspector assessments
fig 7. Inspector assessments
Findings generated by the Inspector:
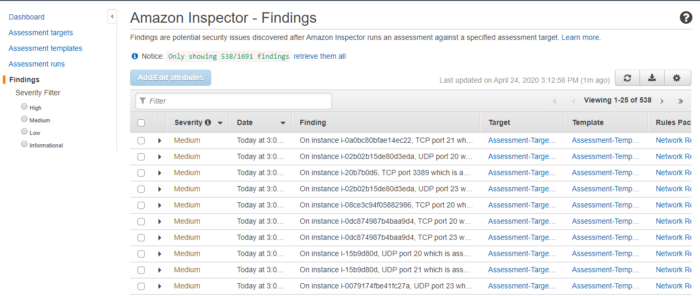 fig 8. Inspector findings
fig 8. Inspector findings
Amazon Inspector rule has severity levels classified as High, Medium, Low, or Informational. This helps you prioritize your response to findings.
Security Hub
AWS Security Hub analyzes findings from these AWS services: GuardDuty, Inspector, Macie, etc. You must have AWS Config service enabled in your account to enable AWS Security Hub to run security checks in the account. Read our blog best security practices for AWS S3 data to learn more about AWS security.
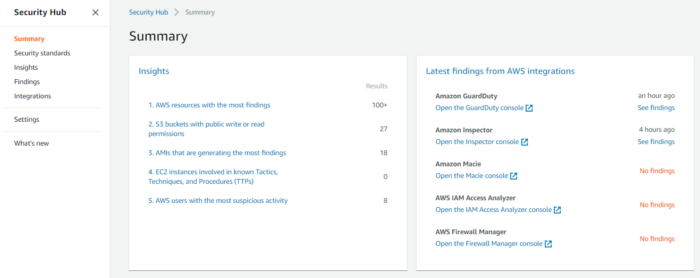 fig 9. Security Hub Dashboard
fig 9. Security Hub Dashboard
Findings generated by the Security Hub:
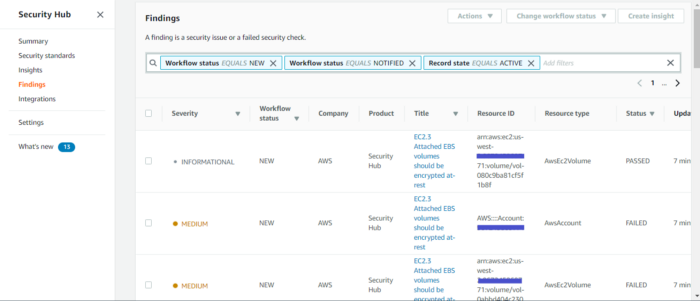 fig 10. Security Hub Findings
fig 10. Security Hub Findings
With AWS CloudWatch Events and AWS Lambda, we have the flexibility to set up alerts based on a security finding generated by AWS GuardDuty, AWS Inspector & AWS Security Hub.
Respond & Recover
In case of a security breach, it's always important to get notified and recover the infrastructure from unauthorized attacks.
Here is how you can get notified using the GuardDuty service.
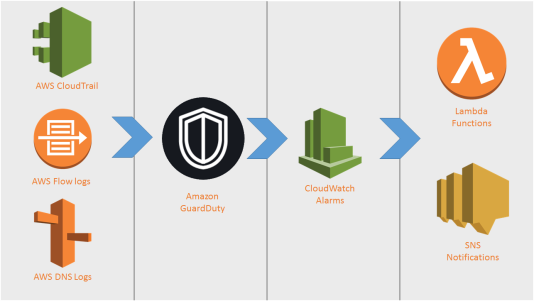 fig 11. GuardDuty Finding Notification
fig 11. GuardDuty Finding Notification
High-level steps to enable notification for GuradDuty security service:
* Enable GuardDuty service in AWS account. * Enable CloudWatch events for GuardDuty service. * Write lambda function to parse CloudWatch event. * Send event details to SNS topic. * Add email subscribers to SNS topic.
You can implement the same notification solution for AWS Security Hub & AWS Inspector service.
Once you get notified, you can take necessary actions to protect the infrastructure from unauthorized attacks. Some examples of automated response actions include patching an AWS EC2 instance, modifying a security group in VPC, rotation of credentials, etc. You can also write a lambda function to auto remediate attacked resources without manual intervention.
For all your requirements of cloud IT solutions, contact us at Clairvoyant.